M2M TO IOT
M2M TO IOT
2.1
INTRODUCTION:
The transition from Machine-to-Machine (M2M) to
Internet of Things (IoT) represents a major shift in the way devices
communicate, interact, and provide value. While M2M systems are limited to the
exchange of data between machines within a closed environment, IoT opens the
door to a more connected, intelligent, and data-driven world, enabling devices
to not only communicate but also analyze, learn, and make decisions
autonomously.
2.1.1
MACHINE-TO-MACHINE COMMUNICATION:
·
M2M refers to a
direct communication channel between machines or devices. The primary goal of
M2M is automation and data exchange between devices (e.g., sensors or
actuators) with minimal or no human intervention.
·
Typically used
in closed, industry-specific applications such as remote monitoring, automated
systems, and SCADA (Supervisory Control and Data Acquisition) systems.
2.1.2 INTERNET
OF THINGS:
·
IoT is an
expanded vision of M2M, where devices not only communicate but also collect,
share, and process data over the internet. It integrates with cloud computing,
AI, big data analytics, and edge computing to offer intelligent
decision-making.
·
IoT enables
devices to communicate with each other globally, not just in isolated systems,
opening the door to smart environments such as smart homes, smart cities, and
industrial automation.
FIG 2.1 – M2M TO IOT
2.1.3 SOME
DEFINITIONS:
·
MACHINE-TO-MACHINE (M2M):
o The exchange of data between devices via wired or
wireless communication.
o Primarily used in controlled environments like
industrial automation and fleet management.
o Does not require human interaction or involvement,
often automated and streamlined for specific operations.
·
INTERNET OF THINGS (IOT):
o A network of interconnected devices that collect,
share, and process data over the internet.
o Extends beyond machine communication by involving
data storage, analysis, and advanced decision-making, utilizing cloud
computing, AI, big data, and real-time analytics.
o Common in smart cities, healthcare, agriculture, and
consumer electronics.
·
SMART DEVICES:
o Devices embedded with sensors, actuators, and
communication modules, which can sense, process, and share information
autonomously or semi-autonomously.
·
CLOUD COMPUTING:
o Centralized platforms (e.g., AWS, Google Cloud,
Microsoft Azure) that offer data storage, computing power, and analytics
services to process and manage the large amounts of data generated by IoT
systems.
·
BIG DATA:
o The massive amount of data generated by IoT devices,
which require specialized tools for processing, analysis, and deriving actionable
insights (e.g., using machine learning and data mining).
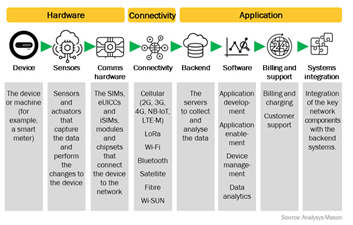
2.2 M2M VALUE
CHAINS:
FIG 2.2 – M2M VALUE CHAINS
M2M value chains focus on the essential components
involved in M2M systems:
o Machines or sensors that collect data (e.g., smart
meters, industrial sensors, RFID tags).
o M2M systems often operate in highly specific sectors
like energy, manufacturing, or transportation.
·
CONNECTIVITY:
o The communication infrastructure (e.g., cellular,
Wi-Fi, satellite networks) enabling data transfer between devices.
o Connectivity in M2M tends to be more localized and
less flexible compared to IoT.
·
MIDDLEWARE:
o Software platforms that enable integration between
different devices and systems. Middleware handles data translation, device
management, and protocol compatibility (e.g., MQTT, CoAP).
·
APPLICATIONS:
o M2M applications are industry-specific, such as
remote monitoring systems in utilities, fleet tracking, and automatic vending
machines.
·
SERVICES:
o Managed services and system integrators who maintain
and optimize M2M networks and operations, ensuring seamless data flow and
reliability.
FIG 2.3 – IOT VALUE CHAINS
IoT (Internet of Things) value chains outline the
processes and components that enable connected devices to collect, share, and
analyze data for actionable insights. Key stages in an IoT value chain include:
·
Device Layer:
Sensors, actuators, and smart devices that capture or respond to data.
·
Connectivity Layer: Networks like Wi-Fi, Bluetooth, cellular, LoRaWAN,
or Zigbee for data transfer.
·
Edge Computing Layer: On-device or near-device data processing to reduce
latency and enhance efficiency.
·
Cloud Layer:
Centralized platforms for storing, processing, and managing data at scale.
·
Data Analytics
Layer: Tools and algorithms for deriving insights from collected data.
·
Application Layer:
User-facing interfaces and software delivering specific functionalities (e.g.,
smart home control, predictive maintenance).
·
Ecosystem and Support: Service providers, developers, integrators, and
partnerships enabling deployment, maintenance, and scalability.
An emerging industrial structure for IoT is
characterized by a layered and collaborative ecosystem designed to support the
development, deployment, and scaling of IoT solutions.
FIG 2.4 – INDUSTRIAL STRUCTURE FOR IOT
Key elements include:
·
DEVICE MANUFACTURERS:
o Companies producing IoT hardware such as sensors,
actuators, and embedded devices.
o Focus on low power consumption, durability, and
interoperability standards.
·
CONNECTIVITY PROVIDERS:
o Telecommunication companies and network technology
firms offering connectivity solutions (e.g., 5G, LoRaWAN, Zigbee).
o Emphasis on secure, reliable, and scalable networks
tailored to specific IoT applications.
·
PLATFORM PROVIDERS:
o Cloud and edge platforms enabling device management,
data storage, and application integration.
o Examples include AWS IoT, Microsoft Azure IoT, and
Google Cloud IoT.
·
DATA ANALYTICS AND AI COMPANIES:
o Firms specializing in data processing, analytics,
and machine learning to derive actionable insights from IoT data.
o Focus on predictive analytics, anomaly detection,
and real-time decision-making.
·
SYSTEM INTEGRATORS:
o Companies integrating diverse IoT components into cohesive
solutions for industries like manufacturing, agriculture, or healthcare.
o Ensure interoperability and scalability.
·
APPLICATION DEVELOPERS:
o Developers creating user-facing applications
tailored to industry needs, such as smart home systems or industrial automation
platforms.
·
SECURITY PROVIDERS:
o Firms specializing in IoTcybersecurity, addressing
challenges like data encryption, device authentication, and network protection.
·
INDUSTRY VERTICALS AND USE-CASE FOCUS:
o Custom solutions targeted at specific sectors like
smart cities, healthcare, logistics, and industrial IoT (IIoT).
o Co-innovation among stakeholders to meet unique
operational demands.
·
REGULATORS AND STANDARDS BODIES:
o Organizations ensuring compliance with global
standards for interoperability, data privacy, and security.
o Examples: ETSI, IEEE, and ISO.
2.5 INTERNATIONALLY
DRIVEN GLOBAL VALUE CHAINS (GVCs):
Global Value Chains refer to the international
fragmentation of production processes, where different stages of a product's
life cycle—design, manufacturing, assembly, distribution, and service—are
spread across multiple countries. GVCs are driven by multinational corporations
(MNCs) leveraging global resources and markets for cost efficiency and
competitive advantage.
2.5.1
CHARACTERISTICS:
·
SPECIALIZATION BY REGION:
o Countries or regions focus on specific stages of
production based on comparative advantages.
o Example: Research and development in advanced economies,
manufacturing in emerging economies.
·
INTERDEPENDENCE:
o GVCs create mutual reliance between nations and
firms. For instance, a smartphone may be designed in the U.S., assembled in
China, and use components from South Korea.
·
TECHNOLOGICAL INTEGRATION:
o Digital tools and platforms ensure coordination and
tracking across supply chains, reducing lead times and costs.
·
STANDARDS AND CERTIFICATIONS:
o Uniform standards (e.g., ISO certifications) ensure
quality and compatibility in the global production process.
2.5.2 DRIVERS:
·
COST REDUCTION:
o Companies outsource production to countries with lower
labor and material costs.
·
MARKET ACCESS:
o Firms tap into local markets by establishing
production and distribution hubs globally.
·
TECHNOLOGICAL ADVANCES:
o Technologies like IoT, cloud computing, and
blockchain facilitate real-time data sharing and operational efficiency.
·
TRADE AGREEMENTS:
o Free trade agreements reduce tariffs and barriers,
promoting cross-border production.
2.5.3
CHALLENGES:
·
Economic Risks:
Dependence on specific suppliers or regions can disrupt production during
geopolitical conflicts or pandemics.
·
Environmental Concerns: Long-distance transportation and high energy
consumption contribute to carbon footprints.
·
Labor Issues:
Exploitation of labor in low-wage regions raises ethical concerns.
2.6 GLOBAL
INFORMATION MONOPOLIES:
Global information monopolies refer to the dominance
of a few large tech corporations in controlling the flow of digital
information, services, and infrastructure. Examples include Google, Amazon,
Meta (formerly Facebook), Apple, and Microsoft.
2.6.1
CHARACTERISTICS:
·
DATA CENTRALIZATION:
o These companies collect and analyze vast amounts of
user data, granting them unparalleled insights into consumer behavior and
market trends.
·
NETWORK EFFECTS:
o The value of their platforms increases with the
number of users, creating barriers for competitors to enter.
·
VERTICAL AND HORIZONTAL INTEGRATION:
o They expand their dominance by controlling multiple
layers of the value chain (e.g., cloud services, hardware, software, and
advertising).
·
INNOVATION HUBS:
o They drive technological advancements through
investments in AI, machine learning, and cloud computing.
·
DIGITAL ECOSYSTEMS:
o Monopolies create interconnected services that lock
users into their ecosystems (e.g., Apple’s ecosystem with iPhones, Macs,
iCloud, and the App Store).
2.7 RELATIONSHIP
BETWEEN GVCs AND INFORMATION MONOPOLIES:
FIG 2.5 – GVCs AND INFORMATION MONOPOLIES
The two phenomena are interconnected:
·
GVCS DEPEND ON INFORMATION INFRASTRUCTURE:
o GVCs rely heavily on digital platforms for
communication, supply chain management, and analytics, which are often
controlled by information monopolies.
·
MONOPOLIES SHAPE GVC DYNAMICS:
o Tech giants dictate the rules of digital trade,
e-commerce, and data sharing, influencing the operational structure of GVCs.
·
DATA AS A KEY RESOURCE:
o Both GVCs and information monopolies capitalize on
data to optimize processes and create value, further cementing the role of
digital dominance in global trade.
2.8 M2M TO IOT:
AN ARCHITECUTRAL OVERVIEW:
`The transition from Machine-to-Machine (M2M) to the
Internet of Things (IoT) marks a significant evolution in connected systems.
While M2M involves direct communication between devices, IoT introduces a more
dynamic, scalable, and interoperable system that integrates devices, networks,
and platforms with advanced capabilities like cloud computing and AI.
2.8.1 KEY
DIFFERENCES BETWEEN M2M AND IOT:
|
Aspect |
M2M |
IoT |
|
Communication |
Device-to-Device |
Device-to-Cloud and
Peer-to-Peer |
|
Scalability |
Limited |
Highly scalable |
|
Interoperability |
Typically
vendor-specific protocols |
Standards-based |
|
Data Usage |
Localized |
Global, centralized,
and analyzed |
|
Intelligence |
Basic device control |
Advanced analytics and
AI |
2.8.2 BUILDING
AN IOT ARCHITECTURE: THE LAYERED APPROACH:
IoT architecture is built in layers, incorporating the
core capabilities of M2M systems while adding flexibility, scalability, and
intelligence.
FIG 2.6 – FIVE LAYER IOT ARCHITECTURE
LAYER 1:
PERCEPTION LAYER (DEVICE LAYER)
This layer corresponds to the hardware components of
the IoT system.
·
Components:
Sensors, actuators, RFID tags, and embedded devices.
·
Functionality:
o Collect data from the environment (temperature,
pressure, location, etc.).
o Execute commands (e.g., opening a valve, turning off
lights).
·
Evolution from M2M:
o While M2M used specific, fixed-function devices, IoT
expands to general-purpose smart devices with modular capabilities.
·
Standards:
o IEEE 1451: Smart transducer interface standards.
o ISO/IEC 30141:IoT Reference Architecture.
LAYER 2: NETWORK
LAYER (CONNECTIVITY LAYER)
This layer manages communication between devices and
the upper architecture.
·
Components:
o M2M protocols like MQTT or CoAP evolve into IoT
protocols such as HTTP, WebSocket, and LoRaWAN.
o Connectivity: 5G, Wi-Fi, Zigbee, NB-IoT, Ethernet, and LPWAN.
·
Functionality:
o Transmit data securely from devices to edge or cloud
platforms.
o Ensure interoperability through standardized
protocols.
·
Evolution from M2M:
o M2M relied on point-to-point connections, while IoT
introduces multi-protocol support, enabling complex networks.
·
Standards:
o IEEE 802.15.4: Wireless communication standard for low-rate
personal area networks (e.g., Zigbee).
o 3GPP: Standards for mobile connectivity (e.g., 5G,
NB-IoT).
o IETF Standards: Protocols such as CoAP and 6LoWPAN.
LAYER 3: EDGE
LAYER
A new addition in IoT architectures compared to
traditional M2M setups.
·
Components:
Gateways, edge computing devices, microcontrollers.
·
Functionality:
o Perform local data processing and decision-making to
reduce latency.
o Act as intermediaries between sensors and cloud
platforms.
o Ensure data is filtered, aggregated, and securely
transmitted.
·
Benefits:
o Reduces bandwidth requirements.
o Enhances real-time response.
·
Standards:
o OPC UA: Open standard for interoperability in industrial
IoT.
o EdgeX Foundry: Open-source edge computing framework.
LAYER 4: CLOUD
LAYER
The IoT's backbone, enabling scalability and global
access.
·
Components:
Cloud storage, computing platforms, and APIs (e.g., AWS IoT Core, Azure IoT
Hub).
·
Functionality:
o Centralized data storage and advanced analytics.
o Support for machine learning, predictive analytics,
and visualization.
·
Evolution from M2M:
o M2M systems typically used localized databases,
while IoT architectures rely on distributed cloud platforms.
·
Standards:
o ISO/IEC 27017: Security standards for cloud services.
o CSA IoT Controls
Framework: Security and privacy
in cloud-hosted IoT environments.
LAYER 5:
APPLICATION LAYER
The user-facing aspect of IoT systems.
·
Components:
Dashboards, mobile apps, and web applications.
·
Functionality:
o Deliver actionable insights to users.
o Provide remote device management and monitoring.
o Enable automation and integration with external
systems.
·
Evolution from M2M:
o M2M interfaces were often basic and vendor-specific.
IoT systems support multi-platform, customizable, and user-friendly applications.
·
Standards:
o OpenAPI
Specification: Standard for building
APIs.
·
ISO 9241:
Standards for user interface and usability.
LAYER 6:
SECURITY LAYER
Ensuring robust security is critical for IoT due to
the expanded attack surface.
·
Components:
o Authentication protocols, encryption standards,
secure firmware updates, and intrusion detection systems.
·
Functionality:
o Protect data and devices against unauthorized
access.
o Secure communication channels and ensure compliance
with global standards like GDPR and HIPAA.
·
Standards:
o IoT Security Foundation (IoTSF) Guidelines.
o NIST IoT Cybersecurity Framework.
o ISO/IEC 27001: Information security management systems.
2.8.3 KEY DESIGN
PRINCIPLES FOR IOT ARCHITECTURE:
·
Interoperability: Use
open standards to enable seamless communication between devices and platforms.
·
Scalability: Design
the system to handle an increasing number of connected devices and data
volumes.
·
Modularity: Use
a modular design for easy upgrades and integration of new technologies.
·
Resilience: Implement
fail-safe mechanisms to handle device or network outages.
·
Data Privacy and Security: Embed security measures at every architectural
layer.
2.8.4 BENEFITS
OF TRANSITIONING TO IOT:
·
Enhanced Insights:
Advanced analytics and AI provide predictive and prescriptive insights.
·
Flexibility: IoT
supports diverse applications, from healthcare to smart cities.
·
Global Access:
Cloud integration enables remote monitoring and control.
·
Cost Efficiency:
Optimized operations reduce costs through automation and predictive
maintenance.
2.8.5 CHALLENGES
IN TRANSITION:
·
Legacy System Integration: Adapting M2M systems to IoT can be complex.
·
Security Risks:
Increased connectivity heightens vulnerabilities.
·
Standardization:
Lack of universal standards can hinder interoperability.
2.8.6 MAIN
DESIGN PRINCIPLES FOR IOT ARCHITECTURE:
·
SCALABILITY:
o Principle: Design to accommodate an increasing number of
devices, users, and data volumes without performance degradation.
o Implementation: Use distributed computing, microservices, and
scalable cloud platforms.
·
INTEROPERABILITY:
o Principle: Ensure seamless communication and integration
between heterogeneous devices, protocols, and platforms.
o Implementation: Adopt open standards (e.g., MQTT, CoAP) and APIs to
bridge compatibility gaps.
·
MODULARITY:
o Principle: Build the system using modular components to allow
easy updates and integration of new features.
o Implementation: Develop independent layers (e.g., perception,
network, application) for flexibility.
·
SECURITY AND PRIVACY:
o Principle: Protect data, devices, and networks from
unauthorized access and ensure user privacy.
o Implementation: Use encryption, authentication protocols, secure
firmware updates, and compliance with standards like GDPR.
·
RESILIENCE:
o Principle: Ensure robust performance under varying conditions
and quick recovery from failures.
o Implementation: Implement fault-tolerant systems, redundancy, and
failover mechanisms.
·
LOW POWER CONSUMPTION:
o Principle: Minimize energy usage to extend device lifespans,
especially for battery-operated IoT devices.
o Implementation: Optimize hardware and communication protocols
(e.g., LPWAN, Zigbee).
·
REAL-TIME PROCESSING:
o Principle: Deliver actionable insights and control with
minimal latency.
o Implementation: Use edge computing for localized data processing.
·
DATA-DRIVEN DESIGN:
o Principle: Make architecture capable of capturing, processing,
and analyzing data for actionable insights.
o Implementation: Integrate AI/ML tools for predictive and
prescriptive analytics.\
2.8.7 NEEDED
CAPABILITIES FOR IOT ARCHITECTURE:
·
Device Management: Ability to onboard, monitor, update, and
troubleshoot IoT devices efficiently.
·
Connectivity: Support
for various communication protocols (Wi-Fi, 5G, Zigbee, LoRaWAN, etc.) and
reliable, secure data transmission.
·
Edge Computing: Localized
data processing to reduce latency and bandwidth usage.
·
Cloud Integration: Centralized data storage, advanced analytics, and
scalable computing resources.
·
Data Security: Robust
measures for data encryption, device authentication, and secure communication.
·
Analytics and Insights: Tools for real-time monitoring, trend analysis,
anomaly detection, and AI-driven decision-making.
·
Scalable Data Handling: Capability to manage high data volumes generated by
large-scale IoT deployments.
·
Interoperable Platforms: Integration of diverse devices and systems within a
unified ecosystem.
·
Energy Efficiency: Mechanisms to optimize power usage in devices and
networks.
·
Compliance and Standards Adherence: Ensure alignment with global regulations and
standards for data protection, privacy, and interoperability.







Comments
Post a Comment